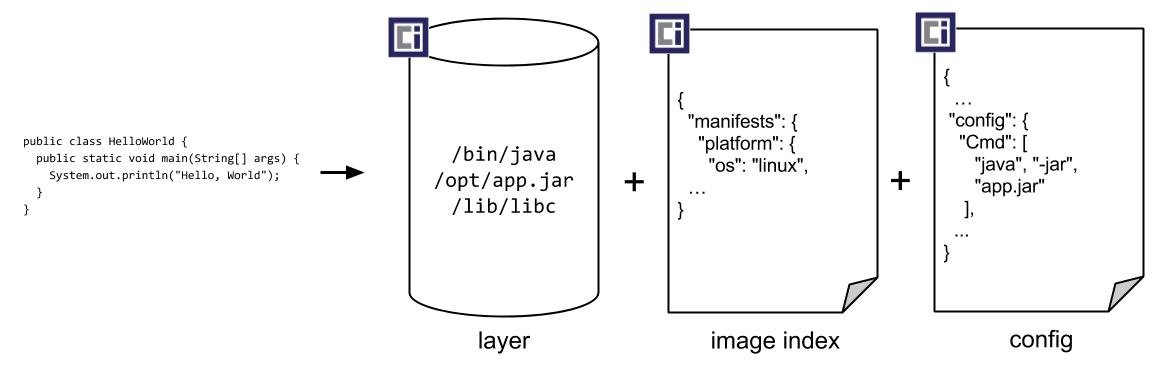
Standard OCI
Open Container Initiative (https://opencontainers.org/)
- Standard budowania i uruchamiania kontenerów
- Ogromna popularność i społeczność wokół Dockera, architektury mikroserwisowej
- Potrzeba ujednolicenia sposobu działania narzędzi i samych komponentów wewnątrz Dockera